Learn how to secure your Flutter project and protect your code with Flutter obfuscation. Discover essential techniques and best practices to safeguard your app’s integrity.
Obfuscation safeguards the Flutter application by making it challenging for malicious actors to reverse engineer or tamper with the code, protecting sensitive data and proprietary algorithms.
Table of Contents
What does the flutter_sharnk application do?
You can download the “Flutter Shrink” application from the Google Play Store to:
1. Discover Flutter Apps: This app helps you identify all the applications developed using the Flutter framework that are currently installed on your device.
2. Explore Utilized Packages: Additionally, it assists you in pinpointing the specific packages utilized within these Flutter-powered applications, giving you insights into the underlying technologies that power them.
All about the Flutter Obfuscation

What is Obfuscation?
Obfuscation in the context of Flutter programming is a deliberate and systematic process of transforming the source code of a Flutter application to make it exceedingly challenging for humans to comprehend while preserving its functionality.
This technique is primarily employed to enhance security and protect intellectual property by obscuring the underlying logic of the code.
During obfuscation, various elements of the code, such as class and method names, variable identifiers, and even the structure of the code itself, are obfuscated or renamed in a way that retains their operational integrity but obliterates their readability.
This involves the substitution of meaningful names with cryptic and non-descriptive labels, making it exceptionally difficult for anyone inspecting the code to discern its purpose or functionality.
What is the purpose of implementing obfuscation?
Obfuscation is crucial because malicious actors can employ readily available tools to reverse engineer APKs, potentially extracting sensitive code and resources.
By obfuscating the Flutter code during the release build, we safeguard our application against such threats.
Obfuscation obscures the code’s structure and logic, making it immensely challenging for attackers to decipher, bolstering security and protecting our intellectual property.
The primary goals of obfuscation in Flutter are:
- Security: Obfuscation adds an additional layer of security to the application by making it arduous for malicious actors to reverse engineer or tamper with the code. This safeguards sensitive data and prevents unauthorized access to proprietary algorithms and business logic.
- Size Optimization: By shortening and simplifying code elements, obfuscation can also lead to reduced code size. This can be especially beneficial for mobile applications, as smaller code sizes contribute to faster download and execution times.
- IP Protection: Obfuscation helps protect intellectual property, as it impedes competitors and unauthorized parties from easily replicating or understanding the unique features and algorithms embedded within the application.
- Performance: While obfuscation primarily focuses on code obfuscation, it can indirectly improve application performance by reducing the size and complexity of the codebase.
In Flutter, the obfuscation process is typically applied during the compilation and build stages using tools like Proguard, which is commonly associated with Java-based Android development.
Flutter-specific obfuscation tools may also be used to cater to the unique characteristics of the Dart language and the Flutter framework.
How to use Obfuscate to protect flutter applications?
To obfuscate a Flutter app, akin to Java’s Proguard, Flutter offers the “–obfuscate” flag, which should be employed in conjunction with the “–split-debug-info” flag.
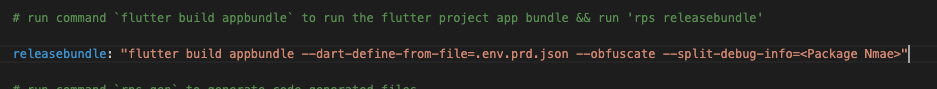
The latter designates a directory for Flutter to generate debug files and symbol maps. These assets become invaluable in the event of needing to de-obfuscate a stack trace for debugging purposes, ensuring that even amid obfuscation, developers can efficiently diagnose issues within the application.
flutter build apk --obfuscate --split-debug-info=<project—package-name>“ — obfuscate” only works with used in combination with “ — split-debug-info”
“split debug info” flag
Crashes and ANRs (Application Not Responding) on Android devices generate a stack trace, essentially a snapshot capturing the sequence of nested functions executed in your program leading up to the point of failure.
This trace reveals class names and associated line numbers, aiding in the identification of the crash’s root cause. However, including this detailed information within the app can inflate its size and consume significant memory during APK compilation.
Enter the “–split-debug-info” flag, a remedy that strips away the data necessary for human-readable stack traces. This not only substantially reduces the app’s size but also generates symbol files.
These symbol files come to the rescue when deciphering otherwise unreadable stack traces, striking a balance between efficient app size and effective debugging capabilities.
How to Read Stack Traces of Obfuscated Flutter App?
To decode a stack trace generated by an obfuscated application and render it human-readable, follow these steps:
- Locate the Corresponding Symbols File: Identify the symbols file that matches your particular scenario. For instance, if the crash occurred on an Android arm64 device, you would require the “app.android-arm64.symbols” file.
- Utilize the Flutter Symbolize Command: Employ the “flutter symbolize” command by supplying both the stack trace, which is typically stored in a file, and the corresponding symbols file.
This command will act as the key to unlock and interpret the otherwise cryptic stack trace, facilitating effective debugging and issue resolution.
Note: Obfuscation is supported by Android, iOS, and macOS
flutter symbolize -i <stack trace file> -d /out/android/app.android-arm64.symbolsConclusion
In summary, obfuscation in Flutter programming involves the deliberate transformation of code into an opaque, cryptic form to enhance security, reduce code size, protect intellectual property, and deter reverse engineering, ultimately contributing to the overall robustness and confidentiality of a Flutter application.
